Facile and Equipment-Free Data Encryption and Decryption by Self-Encrypting Pt(II) Complex | ACS Applied Materials & Interfaces

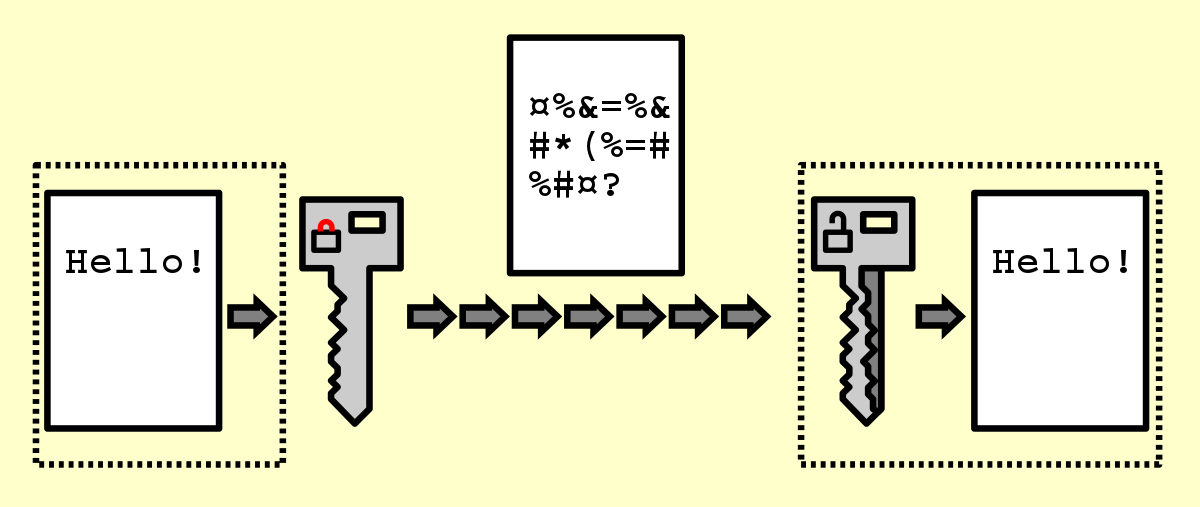
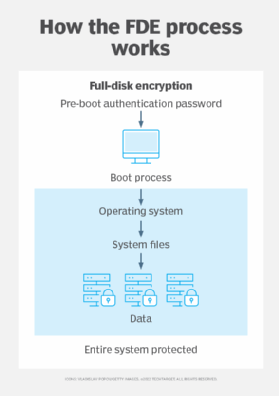
Data Encryption Ensuring Mobile App Security: Safeguarding User Data and Preventing Breaches | by Codepaper | Medium